34+ intrusion detection system diagram
For details see the table below the diagram. There are many reasons or causes for anomalies including system failures human.

Fire Alarm Addressable System Wiring Diagram Pdf New System Sensor Smoke Detector Wiring Diagram Simple Sys Fire Alarm System Fire Alarm Fire Protection System
Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management SIEM system.
. 6 to 30 characters long. To fix an outdated citation hyperlink. Find stories updates and expert opinion.
Up to four tamper pins for static and dynamic intrusion detections Data Flash Optimized for secure storage Address and data scrambling with user-defined key optional Rapid tamper erase on scrambling key and on one user-defined row Silent access for data read noise reduction TrustRAM. Cell growth occurs when the overall rate of cellular biosynthesis production of biomolecules or anabolism is greater than the overall rate of cellular degradation the destruction of biomolecules via the proteasome lysosome or autophagy or catabolism. The word botnet is a portmanteau of the words.
As a company we try as much as possible to ensure all orders are plagiarism free. Since 2017 there have existed supercomputers which can perform over 10 17 FLOPS a hundred quadrillion FLOPS. Up to four tamper pins for static and dynamic intrusion detections Data Flash Optimized for secure storage Address and data scrambling with user-defined key optional Rapid tamper erase on scrambling key and on one user-defined row Silent access for data read noise reduction TrustRAM.
Also intrusion prevention system or IPS is a device or software application that monitors a network or systems for malicious activity or policy violations. Development began on similar systems in the 1960s beginning as a form of computer. Reinforcement learning RL is an area of machine learning concerned with how intelligent agents ought to take actions in an environment in order to maximize the notion of cumulative reward.
In mathematics logic and computer science a type theory is the formal presentation of a specific type system and in general type theory is the academic study of type systemsSome type theories serve as alternatives to set theory as a foundation of mathematicsTwo influential type theories that were proposed as foundations are Alonzo Churchs typed λ-calculus and Per. An intrusion detection system IDS. Anomaly detection refers to the task of identifying abnormal data that are significantly different from the majority of instances and has many important applications including industrial product defect detection infrastructure distress detection and medical diagnosis.
We will guide you on how to place your essay help proofreading and editing your draft fixing the grammar spelling or formatting of your paper easily and cheaply. Mandatory ports refer to ports that must be opened to ensure the proper functioning of the Workload Security system. A self-driving car also known as an autonomous car driver-less car or robotic car robo-car is a car incorporating vehicular automation that is a ground vehicle that is capable of sensing its environment and moving safely with little or no human input.
A facial recognition system is a technology capable of matching a human face from a digital image or a video frame against a database of faces typically employed to authenticate users through ID verification services works by pinpointing and measuring facial features from a given image. Get 247 customer support help when you place a homework help service order with us. Mobile security or mobile device security is the protection of smartphones tablets and laptops from threats associated with wireless computing.
One of the first uses of the term protocol in a data-commutation context occurs in a memorandum entitled A Protocol for Use in the NPL Data Communications Network written by Roger Scantlebury and Keith Bartlett in April 1967. During system testing test data should be separated from real data such as personal information. The field has become of significance due to the.
ASCII characters only characters found on a standard US keyboard. Firewall intrusion detection systems internal encryption access control and personnel controls are examples of layers typically employed to protect enterprise data and programs. A supercomputer is a computer with a high level of performance as compared to a general-purpose computerThe performance of a supercomputer is commonly measured in floating-point operations per second instead of million instructions per second MIPS.
Latest breaking news including politics crime and celebrity. Taipei Mass Rapid Transit MRT branded as Metro Taipei is a rapid transit system serving the areas of Taipei and New Taipei in Taiwan operated by the government-owned Taipei Rapid Transit Corporation which also operates the Maokong Gondola. The IdsM is part of the AUTOSAR Intrusion Detection System IDS.
Take the alphanumeric code at end of the broken hyperlink and add to the end of the link. This perception is perpetuated by. Must contain at least 4 different symbols.
It has become increasingly important in mobile computingThe security of personal and business information now stored on smartphones is of particular concern. More and more users and businesses use smartphones to communicate. Reinforcement learning differs from.
The initial network was approved for construction in 1986 and. Specification of Intrusion Detection System Manager AUTOSAR CP R20-11 1 Introduction and functional overview This specification describes the functionality API and the configuration for the AUTOSAR Basic Software module Intrusion Detection System Manager IdsM. Software maintenance in software engineering is the modification of a software product after delivery to correct faults to improve performance or other attributes.
A botnet is a group of Internet-connected devices each of which runs one or more botsBotnets can be used to perform Distributed Denial-of-Service DDoS attacks steal data send spam and allow the attacker to access the device and its connectionThe owner can control the botnet using command and control CC software. We also have a plagiarism detection system where all our papers are scanned before being delivered to clients. Electronic mail email or e-mail is a method of exchanging messages mail between people using electronic devicesEmail was thus conceived as the electronic version of or counterpart to mail at a time when mail meant only physical mail hence e- mailEmail later became a ubiquitous very widely used communication medium to the point that in current use an email.
Cell growth refers to an increase in the total mass of a cell including both cytoplasmic nuclear and organelle volume. The following diagram shows the default ports in a Workload Security system. 34 digital signature I email T 39 email T.
Computer security cybersecurity cyber security or information technology security IT security is the protection of computer systems and networks from information disclosure theft of or damage to their hardware software or electronic data as well as from the disruption or misdirection of the services they provide. We do not take the issue of plagiarism rightly. All our papers are written from scratch thus producing 100 original work.
Taipei Metro was the first metro system ever built in Taiwan. Take the accession number and add to the end of the link below. Reinforcement learning is one of three basic machine learning paradigms alongside supervised learning and unsupervised learning.
On the ARPANET the starting point for host-to-host communication in 1969 was the 1822 protocol which defined the. Self-driving cars combine a variety of sensors to perceive their surroundings such as thermographic cameras radar lidar sonar. A common perception of maintenance is that it merely involves fixing defectsHowever one study indicated that over 80 of maintenance effort is used for non-corrective actions.
To find a specific citation by accession number.

What Is An Intrusion Detection System And The Types Of It Detection System Id Software

Types Of Ids Behavioral Analysis Content Analysis Analysis

Electronic Security System Importance Classifications And Working Electronic Security Systems Security System Electronics Basics

Computer Security And Pgp What Is Intrusion Detection System Detection Computer Security Network Infrastructure
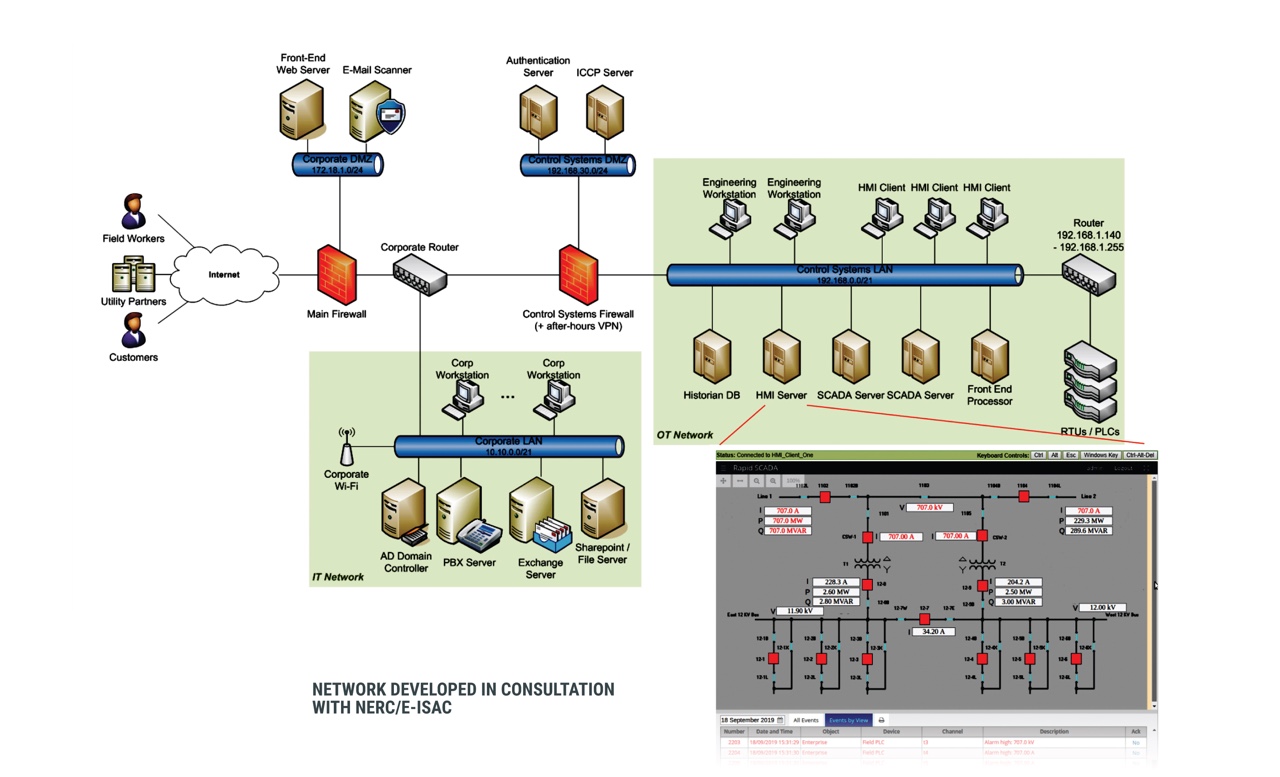
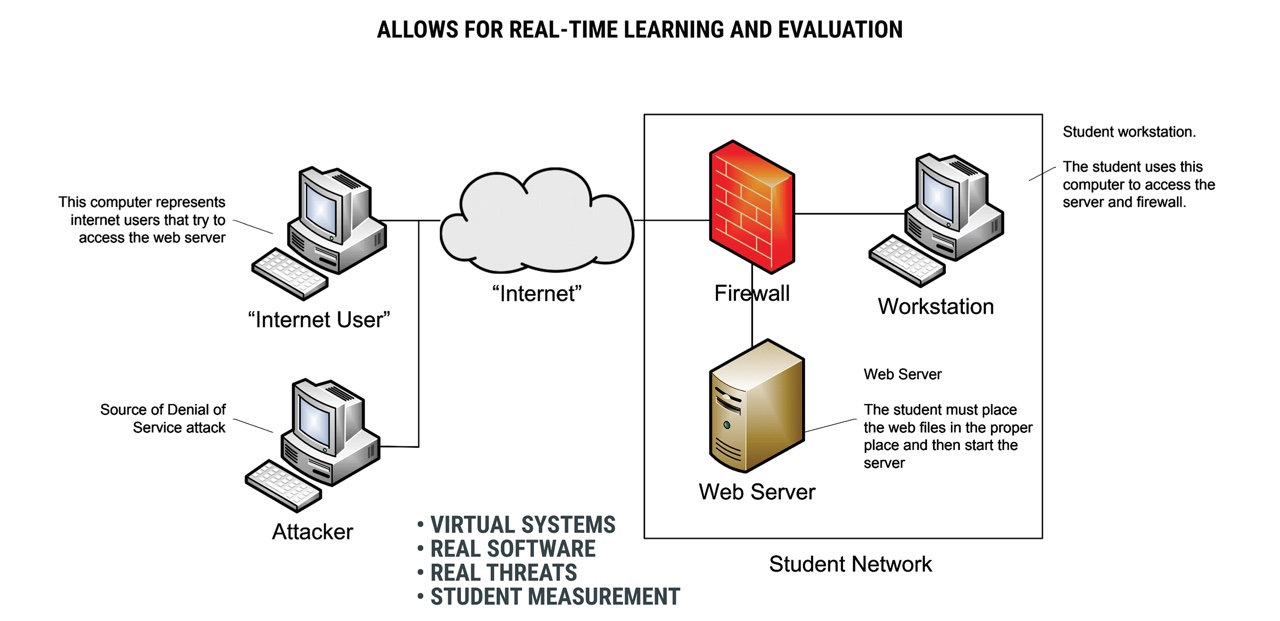
Cyrin Resources

Basics Of Intrusion Detection System Classifactions And Advantages System Detection Electronics Basics

Types Of Fire Alarm Systems And Their Wiring Diagrams Fire Alarm System Fire Alarm Alarm System

Athenalarm Network Alarm Monitoring System In 2022 Alarm Monitoring Alarm System Security Solutions

Ids Vs Ips Ipwithease Network Performance Networking Detection
A Survey Of Artificial Intelligence Techniques For Cybersecurity Improvement Document Gale Academic Onefile

Cyrin Resources

Amazon Com Topdon Phoenix Pro Oe Level Diagnostic Scanner Ecu Ecm Programming Online Coding Bi Directional Control Full System Diagnosis 34 Reset Services 2 Years Free Update Btmobile Pros As Gift Automotive

Probemanager Centralize Management Of Intrusion Detection System Like Suricata Bro Ossec Software Development Hobby Shops Near Me Detection

Fire Alarm System Using Arduino In Few Easy Steps Fire Alarm System Fire Alarm Home Security Systems

Framework Ids Ips Linux Security Pytbull Ids Ips Testing Pytbull Is An Intrusion Detection Prevention Security Tools Framework Web Security
A Survey Of Artificial Intelligence Techniques For Cybersecurity Improvement Document Gale Academic Onefile

Laser Security System Security System Security Alarm Home Security Systems